In Part 1 of our OT Cybersecurity on a Budget series, we looked at low-cost ways to build a strong OT security foundation. Now, we’re diving into how to get the most value out of Cyber Threat Intelligence (CTI)—especially when resources are tight.
Why Threat Intelligence Matters More Than Ever
Today’s threat landscape is anything but static. Threat actors are growing more sophisticated, more targeted, and more interested in disrupting Operational Technology (OT). As the Dragos 2025 OT Cybersecurity Report points out, disrupting Operational Technology (OT) has become more prevalent — and is even a common tactical objective – as demonstrated in the ongoing Ukraine-Russia conflict. This is where quality, actionable Cyber Threat Intelligence (CTI) comes into play.
Threat Informed Defense (TID) is all about using actionable intelligence from CTI to strengthen your detection, response, and proactive defense strategies, making the most out of CTI when both human and financial resources are sparse. This allows Security Operation Centers (SOCs) to not only understand the tactics, techniques, and procedures (TTPs) used by attackers, but to also anticipate and defend against future threats with greater accuracy. By integrating CTI into everyday SOC operations, organizations can align their security posture with the real-world threats that matter most, rather than relying on generic or outdated threat models.
At Edgewater, many of our Federal clients have concerns over OT cybersecurity. In the second part of our series, we will continue to examine Dragos’ 2025 OT Cybersecurity Report and show how it can be applied to the CTI lifecycle. Let’s explore a real-world example of how Edgewater’s experts integrate Threat Informed Defense into SOC operations.
Edgewater’s Threat Actor Scoring
Edgewater has developed a proprietary algorithm that evaluates Advanced Persistent Threats (ATPs) across nine dimensions:
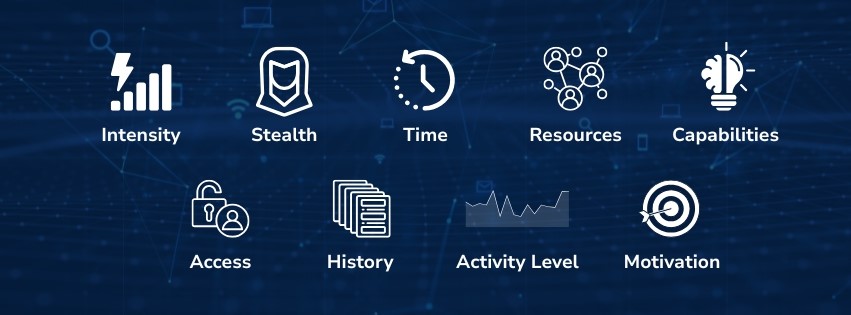
The result is a Top 10 Cyber Threats list of an organization, which is routinely re-evaluated as new intelligence becomes available. Threat actors may move up or down the list accordingly.
The purpose of this list is to provide focus to cyber threat hunt, detection engineering, and offensive security teams. This does not mean that other types of threats should be ignored, but instead CTI teams should integrate threat intelligence from a variety of curated feeds. This assessment helps prioritize the strategic direction of cybersecurity operations when resources are tight. Targeting the threat actors that have the most relevance to our network helps ensure that our proactive defense efforts will have a meaningful impact.
The Dragos report caught our attention because it specifically referenced four of the groups named in the Top 10 list for one of our large Federal clients. TID can use this information to further apply intelligence to the organization by finding the overlap of these groups with TTPs used by more than one threat actor on the Top 10 list. Targeting specific TTPs across multiple threats to the organization can be a force-multiplier when it comes to applying intelligence by other teams. One strategic investment in defense controls could help mitigate multiple threats—saving both time and budget.
For example, APT10 and APT41, both on the Top 10 list and both referenced in the Dragos report, have utilized T1574.001: DLL Search Order Hijacking as a TTP for their campaigns against industrial organizations. Why does that matter?
Because while each group utilizes the method differently, the security controls related to prevention and detection apply to either scenario. Furthermore, this TTP is often undetected by traditional AV and EDR solutions due to execution being sourced from legitimate programs. By identifying that this technique is used by multiple groups on the Top 10 list and is likely missed by traditional defenses, we can create a prescriptive item of focus and prioritization by partner teams in the security organization.
DLL Search Order Hijacking is just one example of a behavior exhibited by a common group of threat actors targeting OT environments. There are several ICS-specific techniques referenced by Dragos that can be tracked similarly to this TTP and may be relevant only to an OT architecture. Edgewater’s Threat Actor Scoring methodology ensures flexibility as it relates to techniques, whether they are specific to OT or a traditional IT cybersecurity architecture.
Bottom Line
At the end of the day, many of the kill chains affecting OT environments begin with intrusions tailored to traditional IT architectures that are non-specific to OT. In either case, Edgewater provides a no-nonsense approach:
– Analyze and prioritize threats to your specific environment based on quality CTI
– Attempt to prevent your next security disaster
– Coordinate with security stakeholders to provide the greatest positive impact on security operations
Stay tuned for the next part of our series, where we’ll explore how this score-driven CTI is applied in a Threat Informed Defense fashion, feeding security teams at your organization.
