Operational Technology (OT) devices are the backbone of federal infrastructure, controlling industrial systems, transportation networks, and energy grids. But as these devices become more connected to IT systems, their exposure to cyber threats increases dramatically. Reducing the OT attack surface has become essential to protect national operations and enable mission continuity.
In May 2025, CISA, along with the FBI, DOE, and EPA, issued urgent guidance urging organizations to remove OT devices from public-facing networks and eliminate default credentials to reduce cyber exposure. Agencies are also encouraged to align with NIST SP 800-82 Guide to Operational Technology (OT) Security Revision 3, which outlines security best practices specific to OT environments.
At Edgewater Federal Solutions, we support federal agencies with tailored Attack Surface Reduction (ASR) services that secure OT environments while meeting high-performance and compliance requirements. By building it right and continuously monitoring, we align best-in-class procedures with NIST and CISA-recommended frameworks.
This article outlines actionable strategies federal agencies can adopt to secure to secure their OT environments against cyber threats and improve operational resilience.
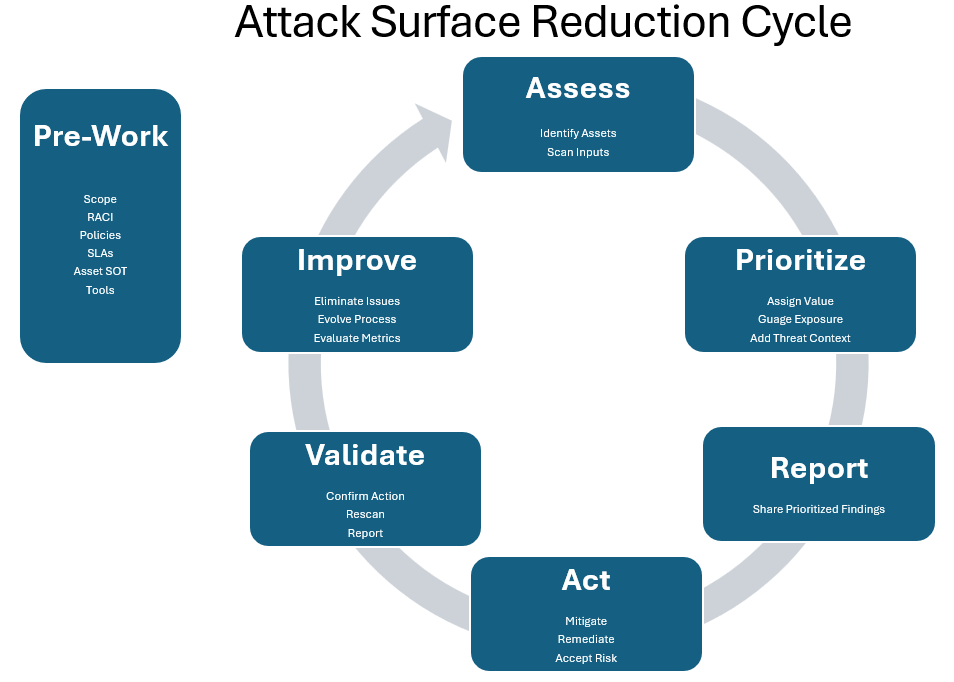
Understanding the Attack Surface
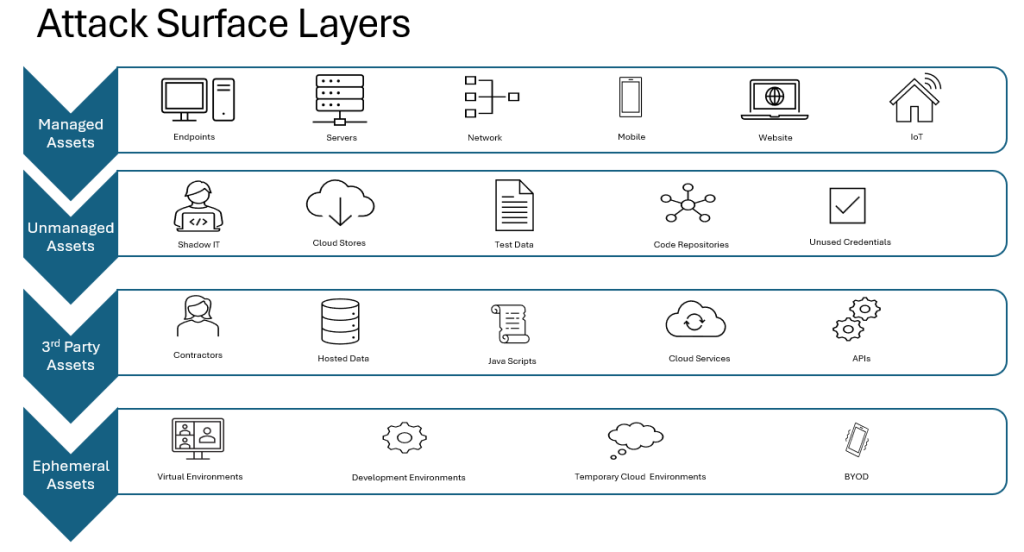
An attack surface refers to the sum of all possible points where an unauthorized entity can enter or extract data from a system. In OT environments, the attack surface includes:
– Network interfaces that connect OT devices to IT systems.
– Unpatched vulnerabilities in legacy systems.
– Unauthorized physical access to control panels or endpoints.
– Insecure remote access mechanisms used for maintenance and monitoring.
– Supply chain risks from third-party vendors or contractors.
Reducing this attack surface requires a multi-layered security approach tailored to the unique characteristics of OT systems.
7 Strategies to Reduce the OT Attack Surface in Federal Systems
1. Implement Network Segmentation
Federal agencies should adopt network segmentation to isolate OT networks from IT and internet-facing systems. Using firewalls, virtual LANs (VLANs), and air gaps ensures that vulnerabilities in IT environments do not compromise OT devices.
2. Enforce Strict Access Controls
Role-based access control (RBAC) should be implemented to restrict unauthorized access. Multi-factor authentication (MFA) should be mandated for personnel accessing OT networks, and least privilege principles should be enforced to minimize potential insider threats.
3. Regular Patching and Vulnerability Management
Legacy OT systems often lack automatic patching mechanisms, making them vulnerable to exploits. Agencies should implement robust patch management policies, regularly update firmware and software while ensuring patches do not disrupt critical operations.
4. Strengthen Endpoint Security
Deploying endpoint detection and response (EDR) solutions tailored for OT environments helps monitor device integrity and detect anomalies. Secure boot processes, encryption, and application whitelisting further reduce exposure to cyber threats.
5. Secure Remote Access
Federal agencies should restrict remote access to OT systems, using Virtual Private Networks (VPNs) with strong encryption and monitoring access logs for suspicious activities. Jump hosts and industrial-specific security gateways can offer additional protection against unauthorized remote connections.
6. Conduct Regular Security Assessments
Routine penetration testing and threat modeling exercises enable agencies to identify weaknesses in their OT infrastructure. Continuous monitoring with Security Information and Event Management (SIEM) solutions ensures real-time visibility into potential threats.
7. Enhance Supply Chain Security
Third-party vendors often introduce security risks. Agencies should vet all suppliers, enforce cybersecurity compliance requirements, and monitor the integrity of hardware and software components used within OT environments.
Bottom Line
Reducing the attack surface of OT devices in federal environments requires a strategic approach that integrates technology, policies, and operational discipline. By proactively addressing their OT attack surface—through network segmentation, strict access controls, patching, endpoint security, and supply chain oversight—federal agencies can stay ahead of evolving threats and significantly strengthen their cybersecurity posture. A proactive security strategy ensures that critical infrastructure remains resilient against emerging cyber threats, safeguarding national interests and operational continuity.
Explore more in our OT Cybersecurity on a Budget series: Part I – A practical guide to building a strong OT security foundation, and Part II – Getting the most value from Cyber Threat Intelligence (CTI) on a budget.
Explore Edgewater’s cybersecurity services to learn how we can help secure your OT environment.
