In 2024-2025 alone, over 19 billion passwords were exposed in global data breaches—and a staggering 94% of them were reused or weak, according to recent cybersecurity reports.
This alarming trend highlights a critical vulnerability in enterprise security: credential reuse across personal and professional systems. Edgewater’s cybersecurity team put its Intercept prototype to the test in a live enterprise environment, uncovering a real-world credential leak that demonstrated the platform’s ability to detect threats before traditional tools even register them.
A Live Credential Leak, Detected Externally
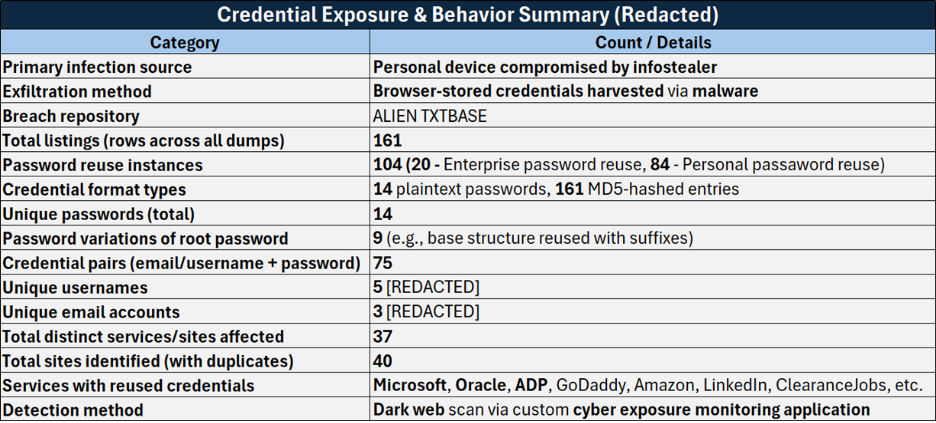
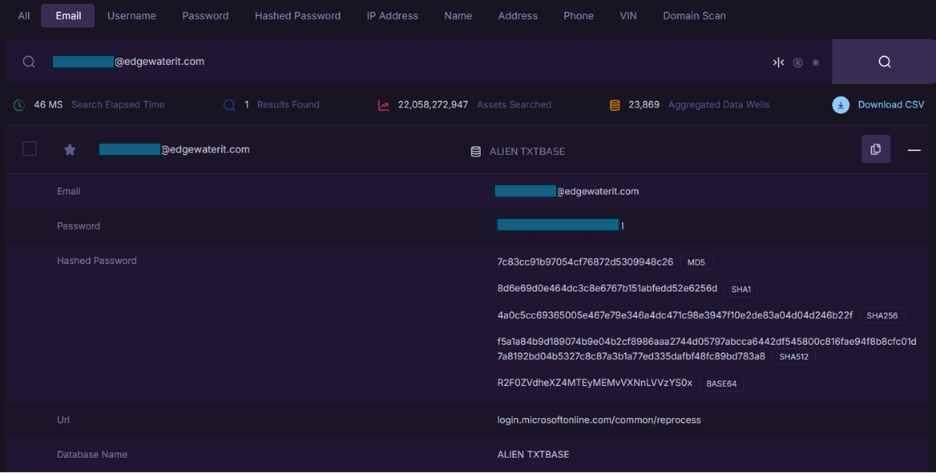
During testing, Intercept flagged an active Edgewater enterprise account whose credentials had been compromised and indexed in the ALIEN TXTBASE breach repository. This wasn’t a simulation or seeded test—it was a real-world exposure involving a live user.
Further investigation revealed multiple failed login attempts targeting the account, confirming that the credentials had not only been leaked but were also actively under attack. The source? A known infostealer malware that had silently harvested the login from the user’s personal browser.
Infostealers: The Silent Threat
Infostealers are lightweight malware tools designed to exfiltrate browser-saved passwords, session cookies, autofill data, and clipboard contents. They’re often delivered via phishing emails, cracked software, or drive-by downloads, making them one of the most scalable and successful tools in a cyber attacker’s arsenal.
In this case, the malware captured the user’s enterprise login credentials and replicated them across 20 separate stealer logs. Because the compromise originated from a personal device, traditional enterprise monitoring tools were blind to the threat.
Sample Findings
Why This Matters
This incident underscores a critical reality: credential exposure can—and often does—occur outside the boundaries of corporate-controlled systems. For Government Agencies, where sensitive data and operational integrity are paramount, this kind of external visibility is essential.
Intercept demonstrated that:
– Enterprise credentials are vulnerable to personal device compromise.
– Password reuse across personal and work systems significantly increases risk.
– Without external monitoring tools like Intercept, these exposures may go completely undetected.
Remediation and Response
Edgewater’s response was swift:
– The compromised password was force-reset.
– The user was notified and educated on the breach origin.
– A security session was scheduled to address password hygiene and infostealer risks.
– Continuous monitoring was activated for the affected account.
– The user received guidance on remediating their personal device.
Key Takeaways
– Personal device hygiene directly impacts enterprise security posture.
– Intercept provides external visibility into user-driven exposures—without requiring endpoint agents or internal access.
– Proactive detection and education are vital to staying ahead of modern threat vectors.
Cyber threats don’t wait for permission—and neither should your defenses. If you’re looking to strengthen your Agency’s resilience against credential-based attacks, reach out to Edgewater to learn how Intercept can help you detect exposures before adversaries act.
Let’s make proactive security the new standard.
