In today’s rapidly evolving cyber threat landscape, the traditional approach of having separate offensive and defensive security teams is no longer sufficient. Enter purple teaming—a revolutionary strategy that bridges the gap between red and blue teams, fostering real-time collaboration to bolster an organization’s defenses. By integrating the adversarial tactics of red teams with the defensive prowess of blue teams, purple teaming transforms cybersecurity from a reactive discipline into a proactive, dynamic process. Whether you’re an executive looking to enhance your organization’s resilience or a security professional aiming to sharpen your skills, understanding and implementing purple teaming can significantly elevate your cybersecurity posture. Let’s explore how this innovative approach can unify efforts, streamline defenses, and ultimately, secure your enterprise against ever-more sophisticated threats.
What is Purple Teaming?
Purple teaming is an advanced cybersecurity strategy that synergizes the offensive tactics of red teams—who simulate sophisticated attacks using adversarial TTPs (Tactics, Techniques, and Procedures)—with the defensive measures of blue teams—who focus on monitoring, detection, and incident response. This continuous, collaborative approach breaks down silos and enhances threat visibility, enabling a proactive defense posture. By leveraging real-time feedback loops and shared intelligence, purple teaming ensures that vulnerabilities are swiftly identified and mitigated, attack detection capabilities are honed, and incident response processes are continually optimized, ultimately fortifying an organization’s security infrastructure against evolving threats.
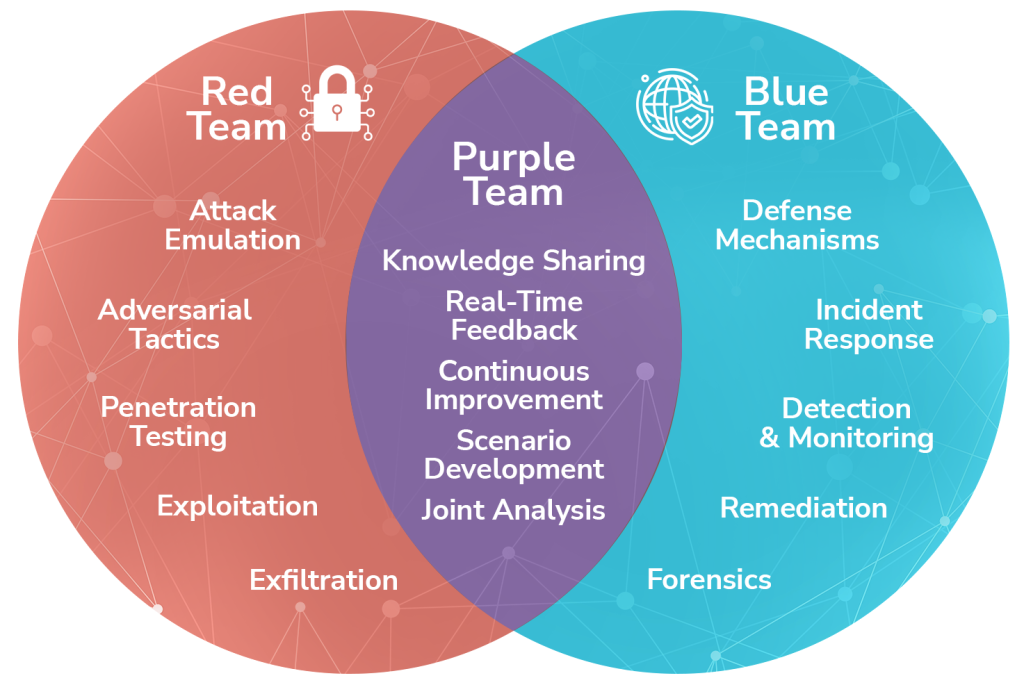
Benefits of Purple Teaming
Implementing purple teaming can provide significant advantages to federal government agencies, which often face unique and substantial cybersecurity challenges due to the sensitive nature of the data they handle and the critical services they provide. It enhances threat detection and response, fosters collaboration, optimizes resources, ensures regulatory compliance, and prepares agencies for advanced cyber threats. Key benefits often include:
Enhanced Threat Detection and Response
Purple teaming fosters collaboration between red and blue teams, leading to more refined threat detection techniques and better monitoring capabilities. By continuously testing and refining their defenses, agencies can ensure quicker and more effective responses to security incidents.
Comprehensive Security Posture
Purple teaming provides a thorough evaluation of an agency’s security posture by integrating offensive and defensive perspectives. This comprehensive approach helps in identifying and addressing vulnerabilities that might be overlooked when red and blue teams work in isolation. The iterative nature of purple teaming ensures ongoing enhancement of security measures.
Enhanced Collaboration and Communication
Federal agencies often have large, compartmentalized security teams. Purple teaming breaks down these silos, fostering a culture of collaboration and shared goals. The collaborative environment promotes the exchange of insights and strategies between red and blue teams.
Cost-Effective Security Measures
Purple teaming allows agencies to make better use of their existing resources by combining the strengths of their red and blue teams. By identifying specific vulnerabilities and areas for improvement, purple teaming helps agencies make more informed decisions about where to invest in new security tools and training.
Regulatory Compliance and Risk Management
Federal agencies must adhere to stringent regulatory requirements (e.g., FISMA, NIST guidelines). Purple teaming helps ensure compliance by continuously testing and validating security measures against these standards. Through comprehensive and continuous testing, purple teaming helps agencies identify and mitigate risks more effectively.
Preparedness for Advanced Threats
Purple teaming allows federal agencies to simulate advanced persistent threats (APTs) and other sophisticated attack vectors. This prepares the defense teams for real-world scenarios and ensures they are equipped to handle complex threats. Regular purple team exercises function as realistic incident response drills, enhancing the readiness of security teams to handle actual cyber incidents swiftly and effectively.
Edgewater’s Recent Purple Team Exercise: MIDNIGHT BLIZZARD’s Password Spray Attack
Recently, Edgewater led the hunt for Midnight Blizzard within our Federal client’s environment. While Edgewater’s threat hunters determined that Midnight Blizzard had not compromised our client’s information, they observed a few critical areas of weakness. In addition to providing recommendations to the client to secure their environment, our threat hunters engaged with our Red Team to develop and execute a Purple Team exercise.
For this Purple Team exercise, we decided to replicate the low and slow password spray attack (MITRE ATT&CK Tactic T1110.003) executed by Midnight Blizzard during their recent attack on Microsoft. Leveraging the expertise of our Cyber Threat Intelligence team, our Red Team was able to mockup an automated low and slow password spray attack capability that would randomly select a client user account known to be in use in their development cloud tenant and attempt a login using a randomly generated password, from a random IP address, and at a random, prolonged time interval.
After two weeks of preparations, our Purple Team exercise lasted for just one week. During this time, our Red Team collaborated with our various Blue Teams including Threat Hunt, CSOC, Fusion IR, Forensics, and Detection Engineering. We discovered that the precisely emulated Midnight Blizzard TTPs would have been successfully blocked by account lockout rules that were already in place.
However, to get real value from this Purple Team exercise, our Red Team began to introduce simple, logical modifications to the initial TTPs, enabling them to bypass the account lockout rules. They were able to successfully attack the client’s development cloud tenant and produce extremely valuable observations that have since enabled enhanced security measures. Based on these observations, our Detection and Security Engineering teams worked with the client to implement improvements that will drastically improve our client’s posture against these types of low and slow password spray attacks.
Are You Ready?
At Edgewater, we recognize the importance of Purple Teaming as a strategic component of our threat hunting and cybersecurity services. Through Purple Teaming, we not only test and improve our defenses, but also contribute to a broader understanding of effective cybersecurity practices. Connect with our team to learn more about how we safeguard the missions of the Federal agencies we serve.
